How does secure enclave work
Asked on 2024-08-05
1 search
The Secure Enclave is an isolated subsystem within Apple devices, designed to keep sensitive data secure. It operates separately from the main processor and is dedicated to protecting critical encryption keys and other sensitive information. Here are some key points about how it works:
-
Isolation: The Secure Enclave is a separate processor, which means it operates independently from the main CPU. This isolation helps protect sensitive data even if the main operating system is compromised.
-
Encryption Key Protection: It starts with the Secure Enclave to protect critical encryption keys. This ensures that sensitive data, such as biometric information and passwords, are securely stored and managed.
-
Secure Boot: Secure boot ensures that the operating system is signed and verified, similar to the process used in iOS. This prevents unauthorized or malicious software from running on the device.
-
Trusted Execution Monitor: This feature ensures that only signed and verified code runs on the device, adding an additional layer of security.
-
Cryptographic Attestation: The Secure Enclave uses strong cryptographic attestation mechanisms to verify the identity and configuration of systems, such as private cloud compute clusters, before any data is sent.
-
Embedded Swift: The Secure Enclave processor uses Embedded Swift, a subset of the Swift programming language, which brings Swift's safety guarantees to the platform. This helps in maintaining the security and integrity of the code running on the Secure Enclave.
For more detailed information, you can refer to the Platforms State of the Union session from WWDC 2024.
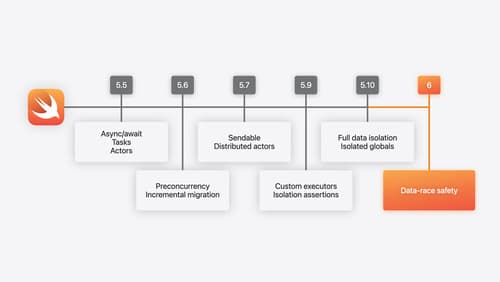
What’s new in Swift
Join us for an update on Swift. We’ll briefly go through a history of Swift over the past decade, and show you how the community has grown through workgroups, expanded the package ecosystem, and increased platform support. We’ll introduce you to a new language mode that achieves data-race safety by default, and a language subset that lets you run Swift on highly constrained systems. We’ll also explore some language updates including noncopyable types, typed throws, and improved C++ interoperability.
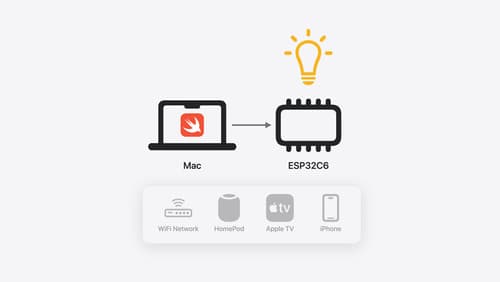
Go small with Embedded Swift
Embedded Swift brings the safety and expressivity of Swift to constrained environments. Explore how Embedded Swift runs on a variety of microcontrollers through a demonstration using an off-the-shelf Matter device. Learn how the Embedded Swift subset packs the benefits of Swift into a tiny footprint with no runtime, and discover plenty of resources to start your own Embedded Swift adventure.

Platforms State of the Union
Discover the newest advancements on Apple platforms.
