how to reverse engineer an app binary
Asked on 2024-07-30
1 search
Reverse engineering an app binary is not a topic covered in the provided WWDC sessions. However, if you are interested in debugging and understanding the control flow of a program, you might find the session "Run, Break, Inspect: Explore effective debugging in LLDB" useful. This session covers various debugging techniques, including working with crash logs and using breakpoints to inspect the state of a program.
For example, you can learn about how to use LLDB to open and analyze crash logs, which can help you understand how a crash happened and investigate the problem further. You can find more details in the chapter on "Crashlogs & starting the program" in the session Run, Break, Inspect: Explore effective debugging in LLDB.
Here is a list of relevant sessions that might help you with debugging and profiling:
- Run, Break, Inspect: Explore effective debugging in LLDB
- Port advanced games to Apple platforms - This session includes a chapter on "Debug and profile with Metal tools" which might be useful if you are working with game binaries.
If you have any specific questions about debugging or profiling, feel free to ask!

Port advanced games to Apple platforms
Discover how simple it can be to reach players on Apple platforms worldwide. We’ll show you how to evaluate your Windows executable on Apple silicon, start your game port with code samples, convert your shader code to Metal, and bring your game to Mac, iPhone, and iPad. Explore enhanced Metal tools that understand HLSL shaders to validate, debug, and profile your ported shaders on Metal.
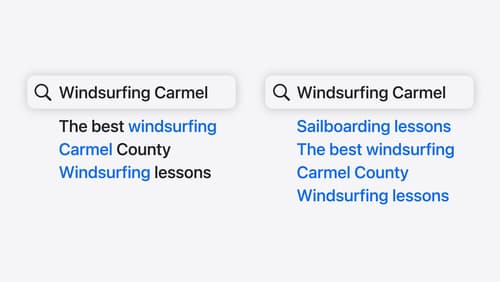
Support semantic search with Core Spotlight
Learn how to provide semantic search results in your app using Core Spotlight. Understand how to make your app’s content available in the user’s private, on-device index so people can search for items using natural language. We’ll also share how to optimize your app’s performance by scheduling indexing activities. To get the most out of this session, we recommend first checking out Core Spotlight documentation on the Apple Developer website.
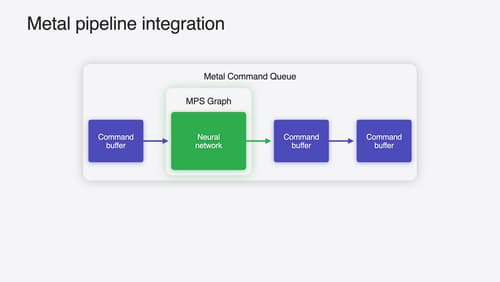
Accelerate machine learning with Metal
Learn how to accelerate your machine learning transformer models with new features in Metal Performance Shaders Graph. We’ll also cover how to improve your model’s compute bandwidth and quality, and visualize it in the all new MPSGraph viewer.
